Welcome to this extensive tutorial for unpacking Jar2Exe. Jar2Exe is a java executable wrapper which works by taking your original java archive, wrapping it into an executable, and executing it through a virtual environment using the jvm.dll provided with each java distribution. It also provides the ability to hide your archive and encrypt the class names making recovery difficult. The goal of this tutorial is to demonstrate how to recover a jar file at the 3 different protection levels provided by Jar2Exe.
In this tutorial, I will be using the file SimpleApp.jar which is included with launch4j. You can protect it with the same settings to reverse along with me.
Tools Needed:
Resource Hacker
Winhex
Ollydbg 1.10+ MemoryDump 0.9 and Olly Advanced or StrongOD Plugin(for advanced ctrl+g).
DJ Java Decompiler
7-Zip or Winrar
Jar2Exe Level 1: No Hiding, No Encryption:
This is the default wrapping level which provides no protection to your java file. As you can see, the Hide class files and Encrypt and hide class files options are left unchecked. This level of protection simply takes your java archive/jar file, concatenates it to the end of the executable, and embeds its java files inside of it. This java archive can be recovered using a hex editor, just like we did with launch4j in the previous tutorial. To begin, we will open sample file called 'SimpleAppNoHide.exe' in winhex. To find the archive, scroll to the bottom of the file. Another option you can try other than scrolling is to search for the ascii string "serial "(with the space). This should take you directly to the archive, but I cannot guarantee that this approach will always be successful.
Once you are here, the first occurrence of 'PK' labels the start of our archive. We can label this as our beginning of block:
Afterwards, we can scroll to the very last byte in the file and label it as our End of Block:
Once you have done so, right click the selected block and click Edit. In the new pane, go to Copy Block -> Into New File.
Afterwards, we can save it as a jar file. I used the name SimpleAppNoHide.jar:
Once we are finished, the program will run correctly, but to be tidy, we need to delete the extra files that Jar2Exe added to our archive. Let's open the archive in 7-zip or winrar(whichever you fancy).
Once it is opened, you can see that Jar2Exe adds an additional directory called 'com'. While some other java applications may use this directory, Jar2Exe adds an additional subdirectory called regexlab.
After entering the com directory, we see that regexlab is the only subdirectory it contains, meaning that the entire com folder is unused and can simply be deleted from the archive, let's go ahead and delete it:
After confirming the deletion, we can close the archive and run the jar file.
If you did everything correctly, the application should run without problems and our work is finished.
Jar2Exe Level 2: Hidden Archive:
With the level 2 protection, Jar2Exe takes our java archive, encrypts it, and adds it as an RCData entry in the resource directory. To find the offset of the encrypted archive, we need to open our executable which I named 'SimpleAppHide.exe' in a resource editor. For this, I prefer resource hacker:
Above, we have located the encrypted data in the "RCData" section of the resource table. In this case, our offset is 46398h. Keep a note of this and open the application in Ollydbg. Once you have it opened, go to the hex dump section and go to the offset above:
Once you arrive at the offset, right click the byte and add a Hardware Breakpoint On Access -> Byte:
Now, let's run the program and wait for the break to occur. We should arrive here:
This loop will decrypt our archive byte for byte. Let's toggle a breakpoint on the instruction after the loop. In this example, the instruction is 00401BE3 > CMP DWOR PTR SS:[ESP+18],EBP. Run the program now and let the decryption complete. Once we break here, the register EAX will contain the location where our decrypted jar file is located and ECX contains its size. Using this information, we are ready to dump the file from memory. To do this, I found a very simple plugin called Memory Dump. It allows you to simply specify a memory address and size to dump those bytes to disk. Let's open the plugin:
To begin, check the field which says End Address / Lenght. This will allow us to enter the length value. Set the Start Address to the value in EAX and the lenght(length) equal to the value in ECX. In my case, the address is 296810 and the size is 11EC. Once you have entered these values, we are ready to dump this to disk.
A limitation of this tool is that you can only save the file with a .dmp extension, but we can easily rename it once we are finished. Simply save it with the name you fancy. In this case I named it as SimpleApp3Hide.dmp for easy recognition.
After a quick renaming, the file is ready to run.
Jar2Exe Level 3: Hidden Archive + Encrypted Class Names:
This is the strongest protection offered by Jar2Exe. First, it changes all of the class file names to gibberish. Second, it encrypts and hides the files just like the level 2 protection. While we can recover the archive with a similar method as in Level 2, we need to take an additional step to repair the class names.
To begin, let's open the application "SimpleAppEncrypt.exe" in a resource editor just as before to acquire the offset of the encrypted RCData:
Our offset in this case is 49398h. Let's note that and open the application in Ollydbg and follow the offset.
Once we arrive at the offset, place a hardware breakpoint on access-> byte just like before.
Run the program an wait for the breakpoint. We should arrive at the following code:
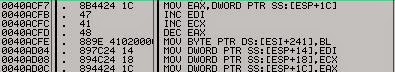
This is the new decryption routine. The instruction 0040ACED-> MOV BYTE PTR DS:[ECX],AL will move each decrypted byte to their new memory location.
According to the code, the address of the memory location where our file is decrypted to can be found at the stack pointer [ESP+18].
The value at ESP+1C contains the size of the memory region. This can be verified by checking the decrement value of the loop.
This code verifies that ESP+1C is the value decremented. ESP+1c is moved to EAX, decremented, and then moved back.
At our current location where the hardware breakpoint landed us, the values at ESP +18 and ESP+1C are the ones we need for our dump. Please note them and target a breakpoint on the instruction outside of the loop.
Once you break here, we are ready to make a dump of the file. But first, I would like to show you the encrypted strings in our archive to give you a glimpse of how jar2exe encrypts them:
As you can see here, the names of our classes and manifest files have been completely obfuscated. As a result, we need to recover these names manually. The way that jar2exe gets the original names for the class is to read them directly from the class file itself. I will show you a simple approach to doing this once we dump the archive.
Now since I am finished digressing, let's dump the file just like before.
In my case, the location of the decrypted file is at 296858 and its length is 1284. We are ready to dump:
Now that we have saved the file, let's rename change the extension to .jar and prepare to extract the contents.
Please note that due to the encryption employed on the names, the file will not run until we correct the classes. Let's extract the contents to a new folder so we can begin repairing.
Once we have extracted the files, let's open the new directory and see the files.
As we can see here, the file names are complete gibberish. The randomly named directories will typically not contain a file and can be deleted. The rest of the files will be the original class and manifest files. To begin the recovery, I like to first identify which file is the manifest. We can usually assume that the manifest will be the smallest file contained in the archive. The manifest.mf file tells the java runtime which file contains the main() class. Without it, the runtime would not know how to execute the code. Let's find the smallest file and open it in a text editor.
As you can see, we have identified our manifest file. This file should be renamed to 'MANIFEST.MF' and placed in a subdirectory called 'META-INF'. Remember that these names are case sensitive and must be typed in all uppercase.
To continue with the rest of the files, let's add a '.class' extension to each of them and open them in your favorite java decompiler. You can read these names with a hex editor if you fancy, but a decompiler makes it a little cleaner. Let's begin with the largest file which is 4kb. I will open it in DJ Java Decompiler.
As we can see here, we have identified the name of this class file as SimpleApp which according to the manifest, contains our main() procedure. The name of the package this file resides in is 'net.sf.launch4j.example'. The dots between these words represent a subdirectory. That means that this class belongs in a folder hierarchy of net/sf/launch4j/example. Let's rename this to class file to 'SimpleApp.class', create the directory hierarchy listed above, and place this file in it.
Now that we have completed this, we just need to go back and follow the same steps for the rest of the files. Please remember that every name is case sensitive. Once you have recovered each of them and placed them into the correct directory(there is only one directory), it should look like this:
Now that we are done, it is time to recreate the jar file. A jar file is simply a zip archive under a different extension. All we need to do is go back to the directory that contains our two folders named 'net' and 'META-INF' and add them to a zip archive.
Now, we simply change the extension of the zip archive to jar and it is ready to run.
Now let's see the finished result:
I hope that you have learned a few things from this tutorial and have walked away with some new knowledge. If something in this tutorial is not clear, please feel free to post a comment and I will try to explain it further. Until next time, happy reversing.
.jpg)
.jpg)





_Jar2Exe%2BWizard_SimpleApp3Hide.jar_.jpg)
_Jar2Exe%2BWizard_SimpleApp3Hide.jar_com_.jpg)
_Jar2Exe%2BWizard_SimpleApp3Hide.jar_.jpg)

.jpg)
_Jar2Exe%2BWizard_SimpleApp3Hide.exe.jpg)







.jpg)
_Jar2Exe%2BWizard_SimpleApp3Encrypt.e.jpg)












_Jar2Exe%2BWizard_SimpleApp3Encrypt_ad4e1605ac83e564147398c9.jpg)






IS there any way for you to make a tutorial about extracting JAR from exe used by Avian (http://oss.readytalk.com/avian/). There is an app called "Best PHP Obfuscator" that uses this and I would appreciate help with extracting the JAR to look at some decompiled code.
ReplyDeleteThanks mate!
nice tut guy! hope it work for me :)
ReplyDeleteTruly Aswm..
ReplyDeleteKeep Sharing.... :)
Br,
Team-URET
In the section where you extract the .jar with the 1st level of encryption(2nd part of the tutorial), it is said: "This loop will decrypt our archive byte for byte. Let's toggle a breakpoint on the instruction after the loop."
ReplyDeleteWhich kind of breakpoint do I toggle? I am confused. Can you give more details please?
Thank you very much for the tutorial!
You just use a standard/execution breakpoint(press f2 on the keyboard). In the picture, the address after the loop is 401be3. That is where you need to set the breakpoint.
ReplyDeleteHi,
ReplyDeleteI cannot find rc data offset in ollydbg. Why?
Make sure you have the advanced ctrl-g option enabled in the olly advanced plugin and follow the OFFSET. When you select offset, make sure that the correct module is selected from the drop down menu of the search box.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteHello . there is little program and the dev use jar2exe+ licence4j to protect it ( it cost about 20usd). When I open it with 7zip I have 4 .jar file ( libraries) but not main jar.
ReplyDeleteI tried as you do but no luck. would you give it try and I can pay you like 10 usd if you can extract the main jar ?
my mail : reverse[@]firelinker[.]com maybe you could record your screen as you do it so I can see what I was doing wrongly. thanks a lot. email me ( as I dont have your mail) and I'll send you the exe. If you suceed send me like a screen capture and I'll paypal you.
Hi ,
ReplyDeleteneed memory dump plugin for ollydgb.
Thanks
Here it is: https://tuts4you.com/download.php?view.2056
DeleteHi
ReplyDeleteits have password can you please give me rar password
Thanks
Hi,
ReplyDeleteIn ollydgb 1.10 there is no option of hardware breakpoint on access .
Thanks
Thanks for this single site your the best ever, many people say that is impossible but you , you are super. i have a file.exe which is encrypted with the first level of encryption, but i am confused from which PK where i position my cursor to select the beginning of block and whick PK i mark as the en of block. and when i try it, i get an error : with this evaluation you can not save file that are larger than 200kb
ReplyDeleteTHank you guys you helped to get a good job . it finally worked, i markey first PK as beginning of block and i went to the end of file i marked from the last bit as end of block. about error: with this evaluation you can not save file that are larger than 200kb. i changed winhex version from to 18 to 17 which is licensed one
DeleteIs there a way to do it with a x64 executable of jar2exe? The x64 instructions are quite different and I'm unable to find the address where the decrypted jar is located.
ReplyDeletehelp me unpack (pack in jar2exe)
ReplyDeletehttps://www.mediafire.com/file/5fkxw5h1ixy06r2/viettel-isdn-locking-4db-20181126.exe/file
thanks !